OUR PARTNERS

















Your trusted partner for managing your cybersecurity challenges
Digital technology brings new opportunities, but also new risks. Our mission is to manage them as effectively as possible, so that you can concentrate on your core business. Thanks to a proactive and comprehensive approach, we integrate technology, processes and human expertise into our services, in order to anticipate threats and protect your data, while keeping your costs under control.
Why entrust your organization's cybersecurity to us?
Flexibility and modularity
Every company has its own needs and requirements. Our aim is to offer you a tailor-made solution, perfectly adapted to optimize the security of your IT system.
Availability and responsiveness
In cybersecurity, responsiveness is a necessity. That’s why we strive to maintain a high level of availability, high rates of problem resolution and rapid response times.
Multidisciplinary expertise
With 20 years’ experience, our 600+ consultants are ready to manage all aspects of cybersecurity, and can provide a team or consultant(s).
Identify and protect yourself against digital threats
Diagnosis
- Security tests & audits
- Regulatory compliance
Protection
- Device safety
- Data encryption
- Loss prevention
- Backup & recovery
Detection
- Application observability
- SOC as a service
- The DevSecOps approach from code to production
Incident response
- Tailor-made solutions
- Phishing response
- Crisis management
Case studies
Our customers say it best!

Reinforcing the security of the Décathlon e-commerce platform
Décathlon wanted to improve the performance of its e-commerce platform. Daily automated audits were carried out on the performance of Cloud accounts and local applications, including the marketplace connector. We hit 100% of our performance targets, in addition to perfecting the connector.

Solve network problems and keep your security up-to-date
In just a few hours, we solved the problem of Internet and network outages for Le Kab. Identifying a configuration conflict between two DHCP servers, we reconfigured the firewall and updated the security rules, stabilizing their connection without additional expense.

Ensuring secure use of the AWS Cloud
An IT company wanted to create its first Cloud environment on Amazon Web Services. We defined policy and governance for multiple organizations and accounts. The result is secure AWS Cloud use and unified multi-subsidiary management, to align AWS Cloud configuration with group practices.

Reinforce access control with dual authentication
A transport company that provides access to its applications via a web portal wanted to reinforce access to one of its applications. We therefore filtered access to the said application, via Citrix and the RedHat SSO IdP in SAML, then introduced multi-factor authentication (MFA) for external service providers.

Guaranteeing third-party application maintenance
The City of Geneva needed to ensure the third-party application maintenance, corrective, evolutionary and preventive maintenance of its applications. We developed two new processes, in addition to handling incidents and requests for changes to applications, and we secured web applications developed in Java.

Making daily life easier for students
The Ecole Hôtelière de Lausanne (EHL) needed a mobile application so that all its students could access all the school’s services. We helped them secure exchanges between the application and the APIs of the various information system applications, using API Gateway.

Enhanced security with Microsoft Purview
The Human Resources consulting firm Vicario entrusted us with the task of strengthening their data security. We deployed Microsoft Purview, activated e-mail encryption via Exchange Online, set up confidentiality labels to prevent accidental sharing, and defined retention strategies so as to ensure legal compliance.

Reviewing and optimizing a Microsoft Intune configuration
An international organization entrusted us with the task of reviewing and optimizing its global Microsoft Intune configuration. We implemented CIS-based security best practices on all Windows 10 and 11 workstations, and optimized device and update management via Intune.

Guaranteeing the security of medical data
As part of an in-depth audit, we helped a healthcare organization resolve performance issues during device enrolment. Based on best practices recommended by Microsoft, we set up configurations designed to increase the level of security.
Our services
Our cybersecurity offers
20 years of expertise at your service
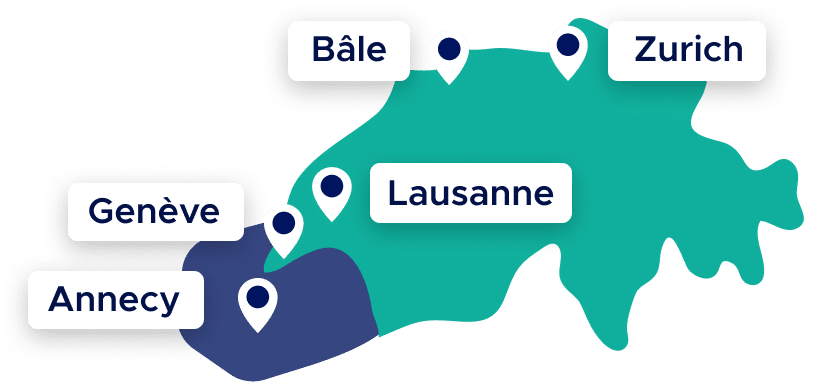
The Qim info adventure began in 2004. 20 years later, our Swiss IT consulting company has 6 offices in Geneva, Lausanne, Zurich, Basel and Annecy. Our experts can help you meet your company’s cybersecurity challenges, whatever your field of activity. Depending on your needs, we support our customers in 2 operating modes: consultancy mode and project mode.
offices in Geneva, Lausanne, Zurich, Basel, and Annecy
consultants at your side
years of expertise at your service
largest IT company in French-speaking Switzerland (ICT journal)
FAQs
We have the answers to your questions!
How does your support work?
We offer you either “à la carte” support, with a package that includes a set number of days, or a monthly subscription, which includes a fixed price for a given number of calls. Our team provides N1/N2/N3-level support and offers high levels of availability: it is always on hand for you.
Do you offer training services so as to raise our employees' awareness about cybersecurity?
Of course. In fact, that is a key part of ensuring optimum security for your IT system. If employees are trained in best practices and made aware of the risks, they will play their part in ensuring the security of your data.
What is a security assessment?
A security assessment is a comprehensive analysis process designed to identify vulnerabilities in your IT infrastructure. It includes penetration tests, an analysis of security configurations and a review of security policies, so as to ensure that your company is protected against current threats.
What cybersecurity services do you offer?
We offer a full range of cybersecurity services, including security assessments, threat management, ransomware protection, encryption solutions, and cybersecurity training for your employees. Each service is customized to suit your company’s specific needs.
How do I know if my company needs cybersecurity services?
If your company collects, stores or processes sensitive data, whether about customers, financial matters or strategy, cybersecurity services are essential. Even small businesses are targeted by cyber-attacks, often due to their inadequate security measures.
What types of threats are you used to managing for your customers?
With over 80 experts and all the cybersecurity professions represented, we can handle any request you may have. From proactive to reactive maintenance, from incident detection to the implementation of automated audits of your IT systems, nothing escapes our attention.
Is a customized solution cost-prohibitive for my SME?
Outsourcing the management of your infrastructure allows you to make significant savings on staffing and maintenance expenses. Additionally, our personalised service model means you only incur costs for the services you actually need.
Book a free call with an expert
An expert will be happy to answer any questions you may have, free of charge and without obligation.
- Free, no-obligation consultation
- We answer all your questions