Do you want to enhance the security of your projects and have heard about Shift Left Security? This article will introduce you to this approach, its advantages, its tools, and the support that Qim info can provide to successfully implement it.
Summary
Shift Left Security: What is it?
The term “Shift Left” literally translates as “shift to the left”. Indeed, the software development lifecycle (SDLC) can be represented linearly. In this case, shifting security to the left means moving security to the beginning of the cycle.
In most cases, security is a late concern that arises at the end of the testing phase and at the time of deployment.
The “Shift Left Security” approach aims to embed security issues even before the code is written, from the planning and design phase. Its goal is to identify and resolve security issues as early as possible.
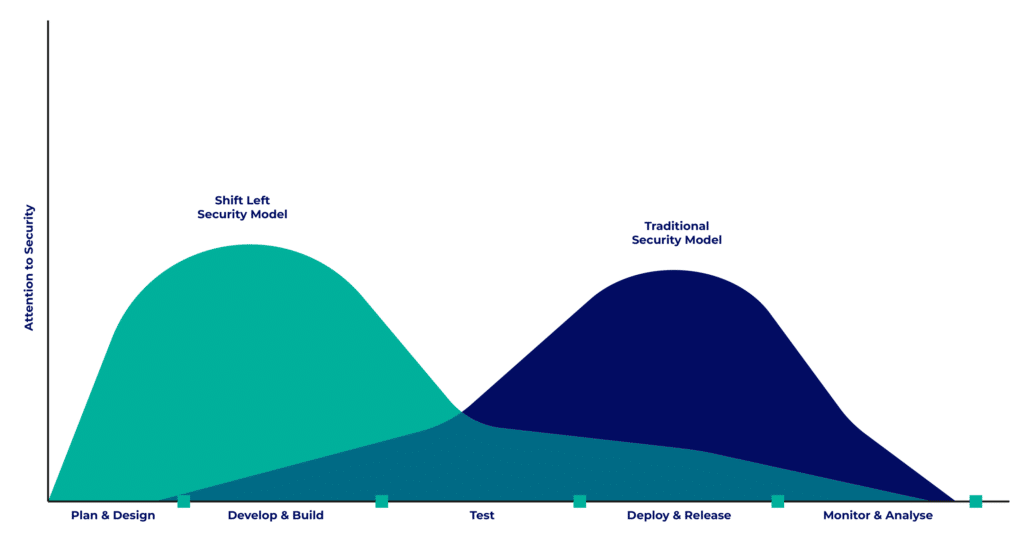
Keep this diagram in mind as there are other strategies with similar names. Among them, let’s learn to distinguish it from Shift Right Security.
What's the difference with Shift Right?
The “Shift Left” approach focuses on the beginning of the SDLC. On the contrary, the “Shift Right Security” strategy focuses on the end of the cycle, from deployment and throughout the operational phase.
This approach aims to apply continuous monitoring in the production environment. Indeed, new threats and vulnerabilities constantly appear. Adopting the Shift Right approach allows for detecting and correcting these vulnerabilities as quickly as possible during operation, before they are exploited.
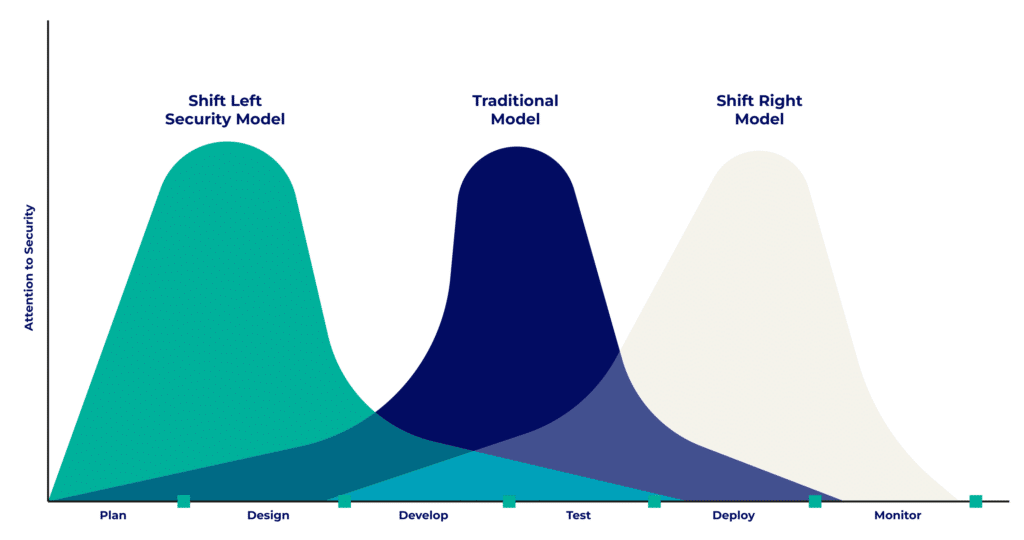
Implementing both strategies allows for optimal security throughout the cycle. While Shift Right is a fairly widespread approach, the Shift Left strategy is considered more innovative and brings many advantages.
What are the advantages of the Shift Left approach?
Early detection of vulnerabilities
Applying the Shift Left strategy to security reduces the time to detect vulnerabilities. Instead of discovering them all at the time of testing, they are gradually identified throughout the development phase.
Teams can then tackle the remediation stage earlier and have more time to apply the fixes.
Reduction in correction costs
This early handling of security reduces correction costs.
Indeed, early detection prevents the accumulation of security issues and thus reduces technical debt and attack vectors on the codebase.
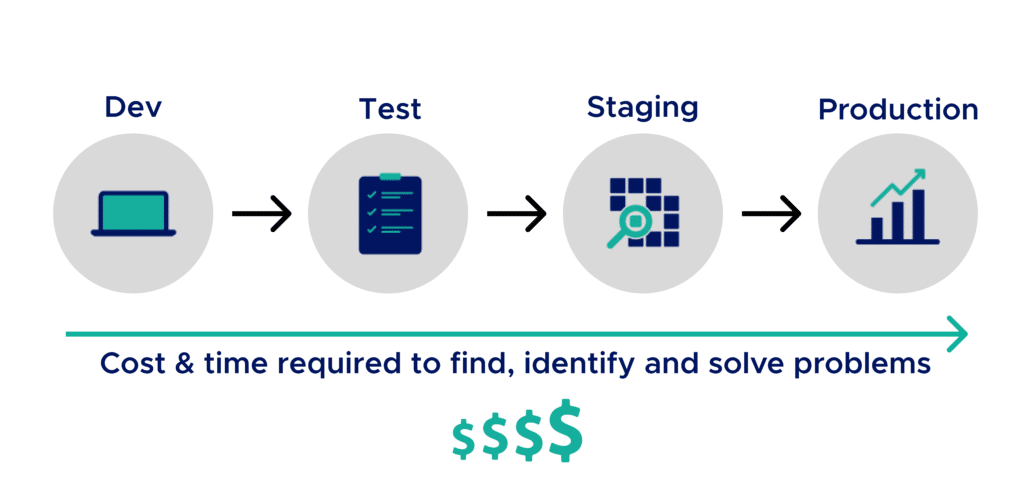
Moreover, the ratio between development, operations, and security teams is quite unbalanced. Applying the Shift Left approach allows giving part of the security responsibilities to the bigger development teams. This frees up time for security teams to perform more specific and higher value-added tasks.
Moving security to the left is therefore a gain in financial and human resources.

Acceleration of time to market
In addition to a monetary gain and better use of skills, applying the Shift Left strategy also reduces time to market.
The progressive and anticipated handling of security issues avoids complex and time-consuming one-off actions, such as corrective interventions in production like Hotfixes.
The market launch is thus no longer blocked by security tests requiring reversals. Indeed, the time to resolve security issues is spread over the early phases of the SDLC.
Improvement of trust and customer satisfaction
Finally, this approach strengthens trust and customer satisfaction. Security is indeed considered a quality criterion by developers, and the product is “Secure by design”.
How to implement Shift Left Security?
Implementing the Shift Left Security approach requires changes to the early stages of the cycle.
First, security must be planned. This means it is important to analyze and identify security needs to take them into account in the solution design. Tests must also be planned to validate compliance with these requirements.
The implementation of security tests must also evolve. They must be broken down into shorter, more targeted tests and occur earlier in the cycle.
The adoption of good development practices allows for reducing sources of errors and thus contributes to the security of the source code. These can impact the choice of dependencies or the management of secrets.
Finally, moving security to the left requires the democratization of “security” tools,such as secret detection tools, dependency and static code analysis, etc… Some must indeed be accessible to development teams, to help them verify the security of their code and correct vulnerabilities. These tools must, however, be understandable, meet their needs, and not be an overly significant additional time burden.
What are the best practices for Shift Left Security?
To ensure the sustainability and proper implementation of Shift Left Security, several best practices can be applied.
First, development teams must be trained. Indeed, with the Shift Left approach, these teams now carry part of the security responsibility. They must then have basic knowledge of security topics that will now concern them, be informed of best practices, and know how to use the security tools entrusted to them.
Teams must also be made aware. They must learn about the impacts of a lack of security and be informed of new threats and risks. To maximize its impact and make this learning more fun, this awareness can take the form of workshops and games.
Collaboration between different professions must also be strengthened. This applies particularly during the planning phase to ensure that the application will be “secure by design“.
Good practices and security policies must be regularly reviewed. An annual review, for example, ensures they are still current, and if not, to bring them up-to-date. Those affected by these changes must be informed, and the implementation must be monitored.
Security measures must also be automated. This ensures their execution, reduces the time burden on teams, and avoids human errors.
Finally, tools must be integrated. This can be locally in the IDEs, but also in the SCMs, in the CI/CD pipelines, or even in the ticketing tools.
What tools are used for Shift Left Security?
Software Composition Analysis (SCA)
SCA tools analyze third-party components of the code such as direct and indirect dependencies. They allow obtaining information on licenses to manage compliance and identifying components with vulnerabilities.
Static Application Security Testing (SAST)
SAST tools enable the identification of vulnerabilities in the source code. These tests are performed without running the application. Errors such as hardcoded secrets or weak encryption algorithms are highlighted. The results of these tests provide the precise locations (files and lines) of potential vulnerabilities.
Dynamic and Interactive Application Security Testing (DAST, Interactive Application Security Testing, IAST)
DAST and IAST analyze the application’s behavior during operation, and detect vulnerabilities such as Cross-Site Scripting (XSS) and SQL injections.
DAST tools do not allow identifying the exact source of vulnerabilities in the code, unlike IAST. However, IAST being hybrid tests between SAST and DAST, they must be adapted to the programming language used.
Container Image Scanning
Container images are generally composed of several layers that may have vulnerabilities. It is therefore important to scan them, particularly the base image, to verify that it does not contain critical vulnerabilities.
IaC Configuration File Scanning
Scanning configuration files can identify vulnerabilities such as poor management of access to instances and network configurations or the exposure of sensitive data.
Among the dozens of existing tools, here is our selection according to three categories.
The Swiss Army knife tools
Some tools offer a very wide range of functionalities. This is notably the case of Snyk and Checkmarx, which are capable of performing SCA, SAST, container image scanning, and IaC file scanning. Checkmarx is also capable of performing DAST.


The open-source and free tools
The Open Worldwide Application Security Project (OWASP) is behind several open-source and free tools. Among them, we find Dependency-Check, an SCA tool, and ZAP, a DAST tool.

Star Tools
Some tools have become references.
This is the case of SonarQube, a quality improvement solution that performs static code analysis (SAST).
In another category, there is Aqua Security, which notably owns Trivy, a scanner that can analyze container images and IaC files.


How much can applying the Shift Left Security approach cost?
Applying the Shift Left approach can be costly. These costs will depend on the company’s needs and constraints.
Costs come from the rates related to tool offers. Indeed, the amount can vary according to the number of lines of code to be analyzed but also the choice of the offer (number of users, features, configuration options).
In addition to these financial costs, it is important to be aware of implementation costs. These are due to the implementation of necessary changes such as user training, but also to the time for analysis and processing of results.
Estimating these costs requires technical expertise to find the most suitable solution.
How can Qim info help you?
The Shift Left security approach aims to implement security as early as possible in the software development lifecycle. It helps better limit vulnerabilities and is a good first step towards DevSecOps. Be careful not to neglect security at the end of the cycle. Do not be content with applying security measures at the beginning, stay vigilant as new vulnerabilities may appear during operation.
To help you adopt and apply the Shift Left approach to security, our Cloud & DevOps Solutions department offers several types of support.
Consulting assignments can be carried out if you want to learn more about Shift Left security and how to implement it in your company. For this, support and exchange workshops can be organized to raise awareness of the impacts of Shift Left security and to find the solution that suits you best. After a phase of analysis of your system and your needs, the department can also use its technical expertise for the implementation and configuration of tools.







