Let's set the stage...
It’s 1 am, and you’re the DPO (Data Protection Officer) of a listed company. You’re sleeping peacefully after a hard day’s work explaining to your colleagues that: “No, we don’t file employee health records on a Teams team to go faster,” when suddenly the phone rings and wakes you up. It’s the CISO on the other end of the line, urging you in a feverish voice to get dressed and call your company’s lawyer immediately: “Our confidential customer files have been stolen and made public; there are already articles on social networks talking about us, the stock market is set to lose 11% tomorrow, and the CEO is furious…”

To help you avoid this situation, we’ve compiled an overview of data protection on Microsoft Cloud to help you see things more clearly (and sleep better at night).
Introduction
With the Covid-19 pandemic, many companies were forced to implement remote working measures for their employees. Many companies opted for Cloud solutions like Microsoft Teams, Google Meet, or Zoom.
Migration to the cloud offers many advantages for businesses: The ability to work and access data from anywhere, flexibility, better collaboration between teams, and more.
Nevertheless, it’s essential to recognise that there are risks when it comes to cybersecurity. Storing data in the cloud can expose it to potential hacker attacks, leaving it vulnerable and managing a virtual environment that appears vast and dynamic can result in a loss of control. It is, therefore, crucial to put in place appropriate security practices and measures to protect documents and data.
For employees, these new ways of working can be confusing. Users often gravitate towards familiar practices based on their habits and daily routines. This includes using their personal computers for work, linking their work email to their personal phones, taking shortcuts to expedite file sharing, and retaining data even after leaving the company. Therefore, implementing specific configurations that restrict or prohibit certain actions is necessary for these user behaviours to maintain the integrity of the company’s information system.
>> Find out more about the skills of our data protection center of expertises


The figures for data theft are rising steadily, and we don’t expect to see any decrease in the near future. Public-sector organisations and SMEs in Europe are targeted and subjected to successful cyber attacks every week, often making headlines. With no training on good security practices for corporate tools and data, and no rules to block risky actions, it’s not a question of IF sensitive data will be leaked or encrypted by Ransomware, but rather WHEN.
In this article, we’ll take a functional look at how to protect data in the cloud, using the principle of “protecting data throughout its lifecycle”.
The primary objective of this principle is to safeguard data from the moment of its creation until its destruction, regardless of the media on which it resides.
The lifecycle of data in the Cloud
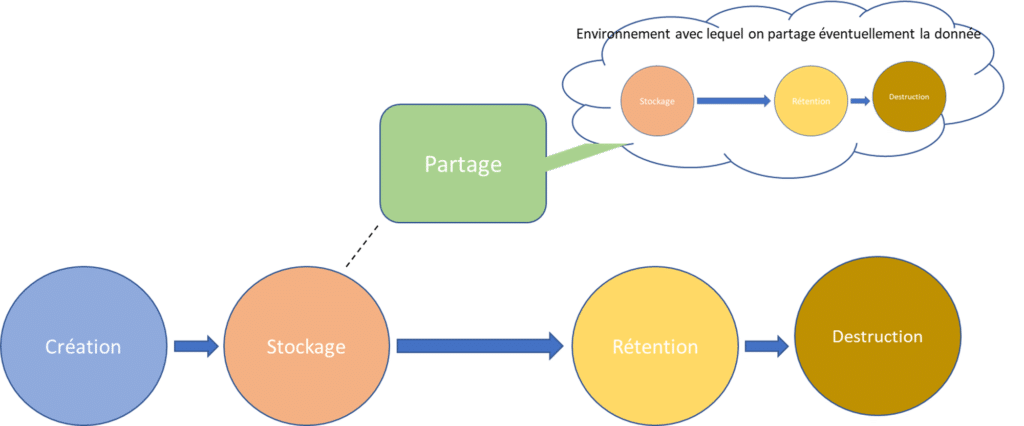
The lifecycle of data in the cloud generally comprises the following stages:
Data can be created from a variety of sources:
– Users creating documents for collaboration or exchanging e-mails
– Applications
– Various Cloud services like log collectors, virtual networks and appliances, collaboration applications that generate data linked to meetings and exchanges, etc.
Data is then stored in Cloud storage systems such as SharePoint Online, Google Drive, or users’ personal OneDrive. But they are also stored in mailboxes, inside applications, as archives, as code in a code repository, etc.
Data is read, modified, and processed. They can also be transferred between different systems/users for sharing and collaboration (attachment, access link sharing…) or within the same management system (Teams). This can lead to a parallel life cycle for the data, as shown in the diagram.
Data is ideally destroyed when it is no longer needed or reaches the end of its lifecycle in the cloud. But sometimes, data can persist and be forgotten when it should be cleaned up. Data may also need to be kept for a longer or shorter period for analysis purposes or if required by law.
At each of these stages, data is exposed to security threats. The lifecycle data protection approach provides cross-functional protection covering all phases and locations of data throughout its existence.
We will now identify which locations are at risk and then define ways of protecting data wherever it may be.
Sources of riks
Devices
The initial line of defence for data protection lies within the user’s various devices, where data is created and manipulated unless your organisation operates on a full Cloud model where data creation and manipulation occur solely on the M365 Cloud platform. When creating an Office-type document, the user often produces it offline from their workstation before sharing it internally or sending it out.
There will therefore be a potentially vulnerable copy of this document on the device. This is also the case for documents downloaded to a workstation or e-mails received and stored locally on the device.
This also applies to mobile devices and equipment. If you allow your users to access their corporate emails or documents on their personal smartphones, you run the risk of exposing your corporate data on this unmanaged device. The same applies to storage and transfer to USB sticks or other physical media: Any downloading or duplication of a document creates a new, independent life for it. And now there are two coexisting documents to protect!
It’s not uncommon to store important documents and then forget to clean them up once the job is done. Or suffering a breakdown and thinking that the repairer can’t have direct access to the data. And yet! Imagine: One of your employees uses their personal phone to receive work-related e-mails. They even download company documents.One day, their phone breaks down, and they bring it to be repaired.
If this third party is unscrupulous, they could access the phone’s documents without your employee’s knowledge…and steal your data.
In rare but possible cases, the absence of data encryption can pose a risk even if the device is protected. Attackers determined to steal the device could access data directly from the hard disk. It’s even possible to retrieve data from hard disk memory after deleting it.
Cloud environment
Here we are referring to the organisation’s tenant, excluding third-party cloud storage.
With poor management of storage location and data access rights, specific data can be accessed and stolen by malicious players.
This applies to internal users and guests or if a user account has been compromised!
backupeverything.co
With data at rest, the risks generally come from a lack of control over access. For example, having reading rights on a document may be enough for it to be stolen.
If the creation and management of Cloud storage spaces are poorly managed, losing control of documents and storage locations is easy. Some documents are kept in storage spaces and consulted years later, even though their creator may have left the organisation. In this case, these files become vulnerable.
Sharing
Document sharing and collaboration: Two words full of promise but, for CISOs, a source of nightmares:
When users share data on the Azure Cloud, they can set permissions to allow each user to access data or not. However, a configuration error can lead to one or more users being granted inappropriate authorisations (access to users from outside the organisation, user groups with excessive access, etc.).
At the same time, file collaboration can lead to the creation of multiple versions, with data stored on different devices or in unsecured locations. In this case, users may not be able to keep track of all versions of their documents, and this could make it difficult to protect sensitive data from leakage.
In the absence of document protection, a simple human error can leak a sensitive document: For example, if the user uses auto-completion when selecting the recipient of an e-mail with an attachment and sends it to the wrong person.
Shadow IT
Shadow IT is a reality with which many organisations have to contend. It refers to the use of technologies and services not approved or managed by the company but used by employees to accomplish their professional tasks. This can include using unauthorised software, applications or Cloud services, and personal devices such as smartphones or USB sticks to store or transfer sensitive data. Moreover, the proliferation of Shadow IT makes it difficult to trace and manage sensitive data, complicating protection against data leaks.
The reasons why employees use Shadow IT are varied. This may be due to restrictions or limitations imposed by company policies, or simply because employees prefer to use tools they consider more practical or efficient in the absence of guidelines or blockages. Whatever the reason, organisations need to take steps to identify and mitigate the risks associated with Shadow IT.
Two concrete examples of Shadow IT:
- A company employee uses a personal Cloud storage application to share files with colleagues because they find it more convenient than the company’s official Cloud service. However, this application is not secure and does not comply with company policies, exposing sensitive data to the risk of theft or compromise.
- A user uses a website that offers artificial intelligence services and enters confidential company data to summarise it. This data is stored and processed by the company that manages the AI and may be leaked or used without the user’s knowledge.
Let’s look at how to protect corporate data throughout its lifecycle.
Data protection

Inventory and classification
Before protecting your organisation’s data, you must know what you want to protect. To achieve this, we must take stock of the documents and data created, used, and transmitted on the organisation’s information system. By taking a global view, it’s easier to determine which data should be prioritised for extra protection and which can be deleted or archived.
Inventory could be carried out as follows:
- Identify all data sources stored on M365 & Azure, including third-party applications connected to the platform, by interviewing key players and exploring the various storage spaces of the M365 tenant.
- Gather information on the data identified: Location, format, the application used to produce it, its owner, date of creation, etc.
- Take stock of the regulations and laws that apply to the organisation: GDPR, local data protection laws, health data, banking data, government data, etc.
- Define data categories to classify data according to importance and risk.
Once the inventory has been taken, it’s time to use the technologies available to label the documents and apply protection according to the label.
Ensuring that documents are correctly labelled is a real challenge.
Two imperfect options are currently available to organisations:
- Train users in document labelling practices.
But relying on their goodwill and the accuracy of the labels they apply carries two risks:
1- The user inadvertently applies the wrong label to a sensitive document, which is then not protected as it should be.
2- The user deliberately applies the wrong label to override sharing rights or with the malicious intent of exfiltrating sensitive data.
- Set up a “smart” system for automatically applying labels to documents. Tools exist to facilitate this labelling process (for example, if a bank card number is detected in a document, a “confidential” label will be applied to the document).
These mechanisms are based on regex-type rules and artificial intelligence algorithms. And once again, problems arise: Firstly, the complexity of using and implementing these algorithms and mechanisms. Time and training resources must be allocated to parametrise AI rules and train the AI that will label the documents.
The second problem lies in the difficulty of obtaining 100% reliable mechanisms. Even AIs trained to recognise sensitive documents can make mistakes if specific parameters and document formats change.
So how do you make it happen? The answer may be a mixture of the two solutions mentioned above.
Some companies use automatic labelling mechanisms where users can manually modify a document’s label. The user must nevertheless justify the change. This justification will be traced and saved if the user wishes to apply a less critical label to the document.
Other organisations opt for “Tips”, or automatic mechanisms that recommend only which label to apply to the document. It’s then up to the user to decide whether or not to borrow the label. These Tips can appear when creating or editing a document or when sending a document by e-mail.
Devices
Specific measures can be implemented to prevent the risks associated with the vulnerability of documents created and stored locally.
First and foremost, it’s essential to establish a clear policy for managing devices such as work computers and cell phones. Opinion is divided on using personal devices in the workplace (commonly known as BYOD or Bring Your Own Device). Personal devices are, by definition, less controlled and secure, and they are all gateways to the organisation’s Cloud environment or data. In the best-case scenario, it would be advisable to completely separate the professional from the personal and thus block all access from personal devices to cloud environments and organisational data. Companies would then have to provide their employees with a computer and business phone package; both set up with the same level of security.
Raising user awareness of good safety practices and equipment use is essential. Implementing strict access control measures, such as two-factor authentication, helps to strengthen device security. Companies can effectively mitigate the risks associated with compromised devices by embracing a holistic approach to data protection, encompassing technical, organisational, and awareness-building measures. This, in turn, ensures the confidentiality of their sensitive information. Concrete examples of preventive action include implementing a device management policy that restricts access to sensitive data to company-approved devices only. To achieve this, the organisation can use mobile device management (MDM) solutions to register and monitor the company’s devices. Disks should also be encrypted using BitLocker, for example.
But first and foremost, safety requires using reinforced and regularly updated devices. The application of data-at-rest encryption on devices provides an additional layer of protection. And yes, a stolen device is still vulnerable even if it has a password to unlock it.
Cloud environment
Effective governance of cloud storage is crucial, with clearly defined responsibilities and management processes.
Labelling and data protection strategies answer many problems, provided they are correctly applied to different documents. The company can implement protection by labels, allowing for graduated levels of protection based on the criticality of different types of documents. In some cases, the company must encrypt data according to the label.
Through these measures, organisations can establish robust access and authorisation management policies, effectively restricting access to sensitive data to authorised users exclusively. They can also regularly monitor storage resources and implement control mechanisms to identify and address suspicious or unauthorised activities. Specifically, this is to detect any instances where sensitive document labels have been tampered with or removed and to identify unsuccessful attempts to extract sensitive documents from the organisation.
The application of a secure data retention and deletion policy ensures that documents do not persist unnecessarily in the Cloud environment, thereby reducing risk.
To accomplish this, companies can employ proactive measures such as implementing monitoring systems and advanced threat detection tools to identify suspicious activities and conducting regular user training sessions on best data protection and security practices.
Sharing
It’s vital to carefully configure sharing permissions in the Azure Cloud, ensuring that each user or group of users is granted the appropriate rights, bearing in mind the principle of least privilege, i.e., giving only necessary rights.
Data protection strategies can go a long way towards mitigating these risks, and here are a few examples of concrete applications:
- A company implements a DLP (Date Loss Prevention) strategy to detect credit card numbers and other payment information in outgoing e-mails and file downloads. DLP blocks the transmission if such data is detected and alerts the company’s security department. This helps prevent the leakage of sensitive financial data and comply with PCI DSS regulations.
- A pharmaceutical company implements a DLP strategy to monitor and control data transfers outside the corporate network. DLP detects any attempt to send confidential data by e-mail or via unauthorised online file-sharing services and blocks the transmission. This helps protect the company’s intellectual property and comply with industry regulations.
Once again, these strategies allow for almost any imaginable scenario:
– Block the sending or sharing of untagged files,
– Apply expiry dates to sharing links for specific file types
– Encrypt files only if they are sent externally,
– Prevent uploads to third-party cloud storage services such as Box, etc.
Continuous monitoring and regular authorisation checks are also necessary to avoid configuration errors that could lead to unauthorised access. At the same time, transparent processes must be implemented to avoid the proliferation of multiple versions on different devices or unsecured servers. Efficient versioning of shared documents plays an essential role.
Governance of information protection will need to evolve as collaboration and sharing practices change within the organisation.
Shadow IT
Before even thinking about protecting data linked to Shadow IT, organisations need to frame the use of Shadow IT and the associated risks as clearly as possible.
Whatever the Cloud platform, many mechanisms are in place to prevent users from accessing third-party storage sites, moving documents to uncontrolled devices or using applications not approved by the organisation.
Companies must start by implementing clear policies and guidelines for using approved Cloud services within the organisation. They will inform employees of the risks associated with Shadow IT and provide secure, compliant solutions.
Effective communication and training on Shadow IT security practices are essential to ensure better data protection.
DLP data protection strategies once again solve most of the risks associated with using Shadow IT. If the company tolerates specific uses, applications, or third-party cloud services, it can use these policies to block documents from being downloaded to these less secure locations. It could apply additional protection and encryption to at-risk data or prevent third-party applications from having read rights to the organisation’s data.
Conclusion
Data protection in the context of the cloud presents numerous challenges. However, adopting a lifecycle approach to data protection offers a comprehensive perspective that encompasses all potential sources of risk to which data may be exposed.
Assessing and identifying risks associated with your data is a crucial step in the right direction. The subsequent step involves an iterative approach, allowing users access only to tools, applications, and procedures that the organisation thoroughly understands and controls.
In any case, it is essential to remember that data is the “gold” of the century, and it would be wise to protect it accordingly.
To read also >> Do you know the Modern Workplace & Workstation department of Qim info?