Have you already implemented the DevOps approach in your teams and wish to enhance security by moving towards DevSecOps?
This article will introduce you to DevSecOps, its challenges, and its benefits. With a set of good practices and some advice, you can integrate security into your business processes.
What is "DevSecOps"?
DevSecOps, which stands for Development Security and Operations, is an evolution of the DevOps approach. Highlighted following the increase in cybercrime, this new culture aims to integrate security earlier and at every step of the DevOps lifecycle.
DevSecOps relies on a strategy known as “Shift Left“, aiming to address security issues from the earliest stages of the software development lifecycle.
The “Shift Right” strategy, in contrast to “Shift Left”, focuses on security after deployment. This allows the identification of vulnerabilities that are difficult to predict and did not appear in the development environment.
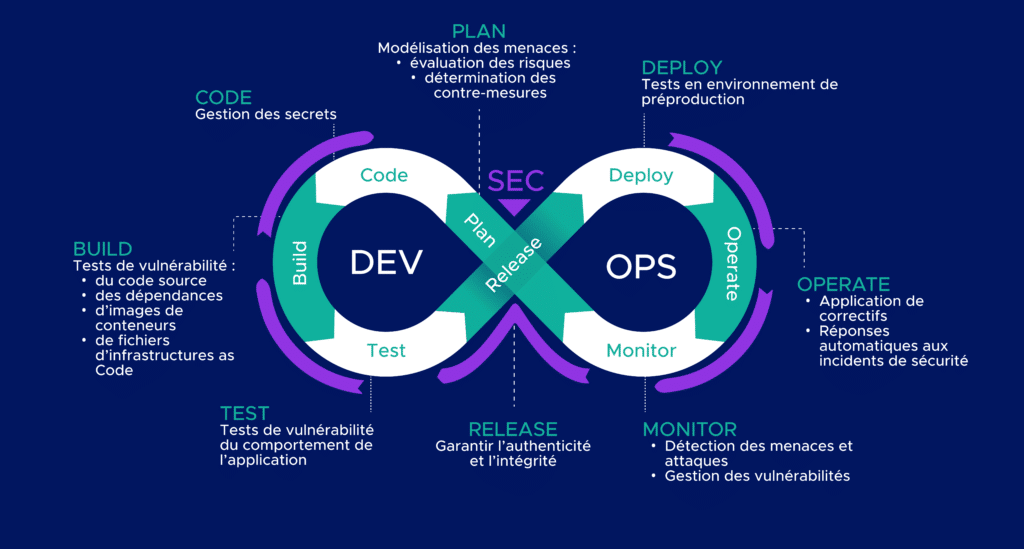
DevOps and DevSecOps: What are the Differences?
An Additional Objective
The major difference between DevOps and DevSecOps is the addition of a security objective.
In DevOps, the application of security is a separate process. Generally, it consists of a checklist verified just before or after deployment to validate security criteria all at once.
However, with DevSecOps, compliance with security requirements must occur as early as possible and be integrated into the chain.
Proactive VS Reactive
The type of security measures also changes.
In the DevOps approach, the measures are reactive, generally put in place following security incidents.
However, DevSecOps is a proactive security approach. Planning and implementing preventive measures aim to reduce risks.
Breaking Down a Third Silo
The last difference is human and organizational.
DevOps aims to break down the wall of confusion between Devs and Ops to promote their communication and collaboration. However, Secs remain apart.
In the DevSecOps approach, all three teams are responsible for security. For this, Secs must be integrated into the DevOps cycle, and the responsibility for security must be shared among the various stakeholders of the cycle. Communication and collaboration must be among three, not just two teams.
Major Challenges of DevSecOps
The first challenge of DevSecOps is to adopt a culture of security. Indeed, each participant in the DevSecOps chain has a role to play. However, numerous professions and individuals interact, all with a different relationship and experience with security. The objective is therefore to raise awareness and provide each individual with basic knowledge tailored to their domain.
Another challenge is securing increasingly complex systems. According to a 2022 Cisco report, 82% of respondents had a hybrid cloud environment, and 92% used a multi-cloud model. This, added to the increase over several years in the number of containers and their orchestration, means that systems now assemble multiple technological components to secure. The objective is thus to facilitate security with a more targeted and progressive implementation.
The last challenge is reconciling strong security constraints with the shortest possible Time to Market (TTM). Reducing the TTM is indeed one of the objectives of DevOps. However, it may be increased if pre-deployment security tests detect vulnerabilities requiring heavy changes and rollbacks. The objective of DevSecOps is therefore to better control and anticipate the TTM by implementing security progressively.
Now that we are aware of these challenges, let’s look at the advantages of DevSecOps.
The Benefits of Working According to This Approach

Implementing this new approach can bring many advantages. The first is better control of times and costs. An upfront consideration of security issues and their resolution can avoid unpleasant surprises. With DevSecOps, the establishment of security measures is planned and quantified, avoiding costly and time-consuming fixes.

DevSecOps also allows for increased customer trust and satisfaction. Indeed, security is now a priority and is considered a quality criterion. Customers have the assurance of having a product compliant with legal obligations and other security requirements.
This approach is also beneficial for technical teams as it streamlines the implementation of security. Rollbacks with significant changes can be poorly received and misunderstood by teams. The progressive implementation of lighter measures allows teams to maintain their agility.
Lastly, don’t forget that the main advantage is the increase and improvement of security. Avoid the disastrous consequences that your company could face, such as when dealing with theft or data loss.
However, benefiting from these advantages requires the implementation of the following good practices
Good DevSecOps Practices
Raising Awareness and Training Teams
DevSecOps being a new culture, the involvement of teams in its implementation is essential. For this, it is important that they are sensitised and trained on the topics concerning them. They will then integrate new security habits, for example, good management of secrets. This one is less complex to implement than other practices but can nevertheless generate critical vulnerabilities.
Uber Case Study
In 2016, Uber experienced a data breach due to the use of an AWS access ID and password in code stored on GitHub. The company paid $100,000 to the hackers to keep the data undisclosed.
Planning Security
To integrate security as early as possible in the cycle, it is necessary to anticipate its implementation. To do this, a phase of reflection and analysis helps to identify potential threats and risks to the project, and to determine if countermeasures are necessary. It is during this stage that security tests are chosen and planned.

Automating Security Tests

These allow for the identification of vulnerabilities in both container images and third-party code, as well as in the formality and runtime behavior of the source code.
Automating them throughout the cycle allows more time for teams to perform high-value tasks.
Implementing Security Monitoring

It is also necessary to monitor security events. For this, the monitoring system must gather various information and correlate it to detect threats and security incidents. After their identification, the monitoring system must be able to issue alerts. Finally, the security status of the system must be visualizable.
However, integrating these best practices does not guarantee the proper implementation of DevSecOps.
How to implement this approach in your company?
The implementation of the DevSecOps approach is similar to that of DevOps. Therefore, it is necessary to adopt this new culture and integrate its new processes and tools.
Datadog Case Study
Security engineers temporarily joined development teams to raise awareness about security. This made it clear to the Devs that the Secs were there to support them, to help improve the quality of their code by enhancing its security. This also made the Secs realize that they could lack agility and be too slow compared to the developers’ production pace.
The goal was then to automate security using tools. Several conclusions were drawn:
- Security test feedback must be fast to keep up with the Devs’ pace.
- Alerts should not necessarily be sent to security teams. Some can be sent to the Devs with resolution instructions.
After using market tools, they decided to create their own tools for static testing and software composition analysis, more suited to their needs.
Conclusion
The DevSecOps approach aims to integrate security throughout the DevOps chain. This facilitates the securing of critical or complex systems and improves customer satisfaction and cost control.
However, this approach is not suitable for all projects. The choice of its implementation should be made after analyzing the system and its security needs. Moreover, not all DevSecOps tools and processes are suitable for all projects. The level of its implementation will also depend on other factors such as team skills, time, and resources allocated to the project.
Our Cloud & DevOps Solutions department is available to discuss your DevSecOps projects and assist you in its implementation.







