If you’ve heard of the DevSecOps philosophy and would like to implement it in your projects, this article will introduce you to various DevSecOps tools, their respective advantages and disadvantages, and Qim info’s recommendations!
Why choose DevSecOps?
Before getting into the details, here’s a quick overview of DevSecOps.
The DevSecOps approach aims to strengthen security by including it at every stage of the software development lifecycle – it’s an evolution of DevOps that offers numerous advantages. It not only reduces the number of vulnerabilities, but also the time it takes to detect them, consequently also reducing the amount of time it takes to remediate them. This allows us to better control costs as well as project progress.
Implementing and adopting an effective DevSecOps approach requires a number of tools. Let’s take a look at some of the most useful ones.
What are DevSecOps tools?
A DevSecOps tool is a device or means of facilitating the implementation of the DevSecOps approach. These tools come in the form of software or platforms. They are made available to development, security and operations teams so that they can increase their efficiency and improve the integration of security throughout projects.
All of these actions can be performed using one or more tools. Don’t worry! All of the acronyms are explained in further detail below.
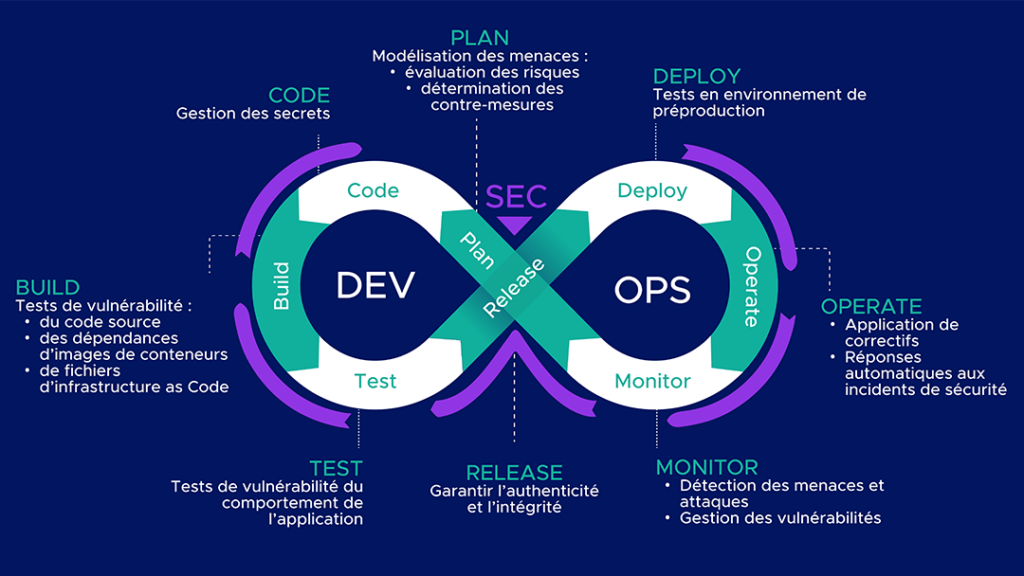
What are the different types of DevSecOps tools?
- Software Composition Analysis (SCA)
SCA tools analyse third-party code components, such as direct and indirect dependencies. They allow information about licences to be obtained, facilitating compliance management and the identification of components with vulnerabilities. Some SCA tools can generate files called SBOM (Software Bill of Material): these list all third-party and open source components integrated into the code to ensure they can be traced. - Static Application Security Testing (SAST). SAST tools help identify vulnerabilities in source code.
These tests are performed without running the application. Errors such as hardcoded secrets or weak encryption algorithms are highlighted. The results of these tests provide the precise locations (files and lines) of potential vulnerabilities. - Dynamic Application Security Testing (DAST)
.DASTs enable the analysis of application behaviour during operation. To do this, requests are sent to the application and the responses are examined for vulnerabilities. Flaws such as Cross-Site Scripting (XSS) and SQL Injection can be detected, but their sources are not precisely identified. DASTs are usually performed after SASTs since they require a working application. - Interactive Application Security Testing (IAST)
IAST is a hybrid test between SAST and DAST. They work through agents in the application’s runtime environment, which analyse security problems as and when they happen. They detect vulnerabilities similar to those detected by DASTs and are able to return the location of the vulnerability in the source code, just like SASTs. However, they need to be adapted to the programming language and are not capable of detecting all vulnerabilities because they do not monitor the entire code. - Scanning container images
.A container is created from an image, which is made up of several layers including the base image. It is therefore important to ensure that it comes from a reliable registry and to check the vulnerabilities it contains. For this purpose, scanners are available to identify vulnerabilities in images and to provide suggestions for image versions that contain fewer vulnerabilities. - Scanning Infrastructure as Code configuration files
In the case of Infrastructure as Code (IaC), performing a scan of configuration files can identify vulnerabilities such as mismanaged access to instances and network configurations, or the exposure of sensitive data. - Security Information and Event Management (SIEM).
A SIEM collects and aggregates data from various event logs. These elements are then correlated so that suspicious activities and threats can be identified and prioritised. Alerts are issued once they are detected, thereby reducing the Mean Time To Detection (MTTD). A SIEM also generates numerous dashboards to provide an overview of system activity. - Extended Detection & Response (XDR)
. An XDR solution is a multi-layered monitoring tool for endpoints, firewalls, servers and Cloud workloads. It collects and analyses data, which it uses to detect and respond to threats. - Security Orchestration, Automation and Response (SOAR)
. The main aim of a SOAR solution is to detect and block attacks. To achieve this, it includes tool orchestration functions, as well as task automation through playbooks that trigger automated responses. This platform centralises the management of security incidents and can be fed with data from a SIEM.
Top 7 DevSecOps tools
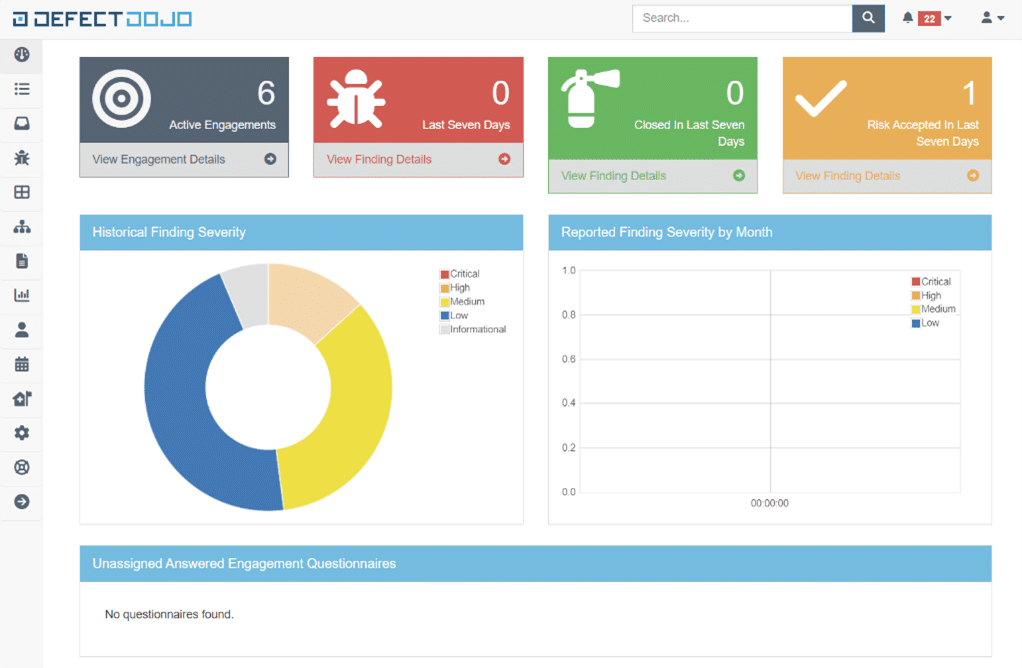
1. DefectDojo
DefectDojo is a vulnerability management tool.
It’s a platform that aggregates reports from different security tools to centralise their vulnerabilities.
It can be self-hosted or available as SaaS. For the purposes of this comparison, we tested the demo platform available online.
Who is it aimed at?
Companies wishing to secure their systems on a large scale and who are ready to hire a DefectDojo manager.
Pros
- Centralise vulnerabilities and the management thereof: allows you to list and manage all vulnerabilities from different tests on different products.
- Customisable dashboards to track security progress.
- Integration possibilities: numerous well-known SAST, DAST and infrastructure scanning tools such as Checkmarx, SonarQube and Trivy.
- Its API for providing test reports to DefectDojo and obtaining information from outside the platform.
Cons
- A steep learning curve. The platform offers a wealth of information and configuration options. Getting the hang of it will take time and so it needs to be a gradual approach to avoid discouraging new users. Integrate products gradually, starting with the most critical.
- The price of Dojo Pro.
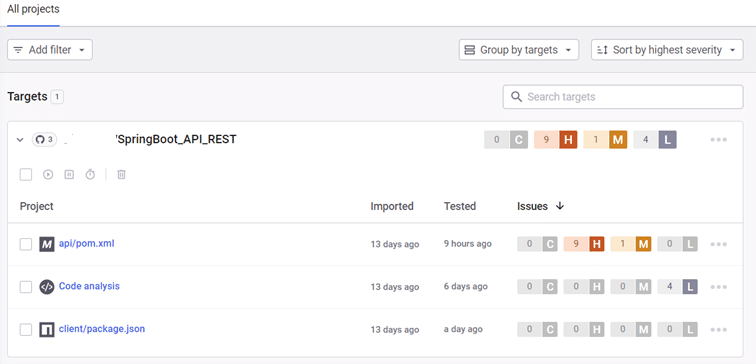
2. Snyk
Snyk offers several products:
- Snyk Code (SAST)
- Snyk Open Source (SCA)
- Snyk Container
- Snyk Infrastructure as Code
- Synk App Risk ASPM
Snyk integrates not only with CI/CD pipelines, but also with IDEs and container registers.
For the purposes of this comparison, we’ve tested the free version of Snyk with its Web application and VS Code extension.
Who is it aimed at? Companies looking for a multi-disciplinary tool who already have existing expertise in security.
Pros
- Ease of integration in an IDE: easy to install, user-friendly, ability to choose test modules and the severity level of vulnerabilities to be displayed.
- The Web application: to get an overview of projects, open pull requests in Github, or manage the organisation and its members.
Cons
- Suggestions for remediation. In our tests, many of them were missing or included examples that had nothing to do with the code that was analysed. This can be frustrating and time-consuming for developers.
- Analysis time. In the IDE, it is impossible to target the files to be analysed. For large-scale projects, this means a lengthy analysis process that slows down developers.
3. SonarQube
SonarQube is a code quality tool that performs static tests (SAST) for multiple languages.
It can be integrated into CI/CD pipelines.
For the purposes of this comparison, we tested the Community version of SonarQube.
Who is it aimed at? Companies who have no security expertise but who still want to improve the security levels of their projects.
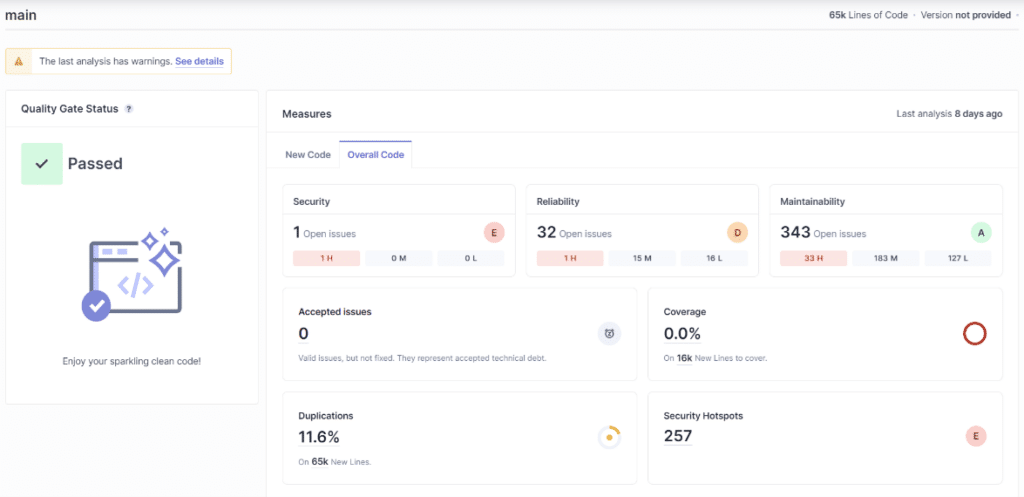
Pros
- The graphical interface. It’s easy to understand, despite its many criteria and configurations.
- Problem management. You can assign them to people, manage their lifecycle (accepted, false positive, confirmed, repaired), and assign custom tags.
- Quality Gates. They help define a minimum level of quality for projects. Test results are compared with predefined criteria, to validate or reject the project.
- Specific suggestions for remedial action, adapted to the project.
Cons
- The price. It varies depending on the version and the number of lines of code to be analysed and can be very high.
- Integration can be tricky, due to incorrect instructions in the documentation and unclear error messages.
4. Trivy
Trivy is a vulnerability scanner for Infrastructure as Code containers and configuration files.
Trivy is installed and used via command lines.
For image scanning: trivy i [nom de l’image]
To scan IaC configuration files: trivy config [IaC directory]
After the scan has been completed, the total number of vulnerabilities and their ranking by severity are provided.
For the purposes of this comparison, we tested Trivy on Debian 12.5.0, scanning various images and Dockerfiles.
Who is it aimed at? All companies using containers and IaC.
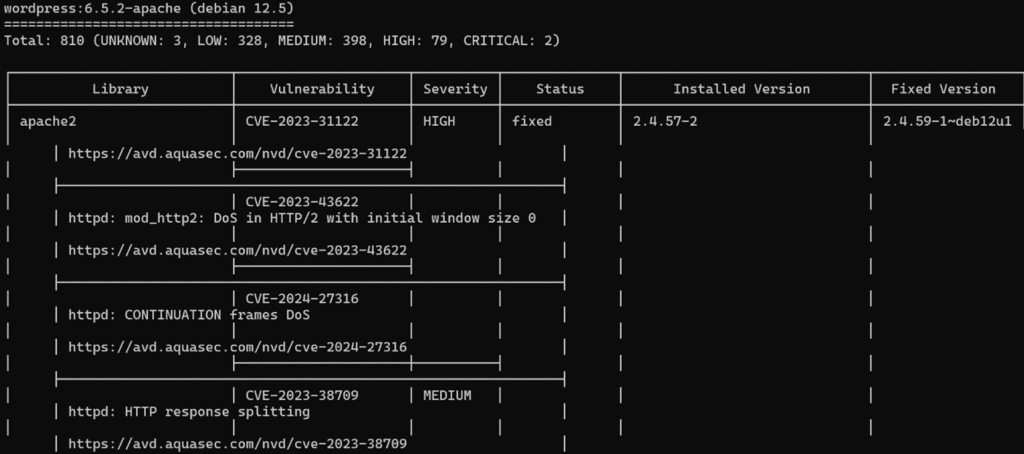
Pros
- Ease of use. A single command line is all that’s needed and parameters can be added to filter by severity, for example.
- The scan is very quick to complete.
- Links to pages in the Aqua Security vulnerability database. It contains both CVE and misconfiguration pages.
Cons
- The absence of a graphical user interface, which may hold some users back.
- Lack of suggestions for remediation or vulnerability reduction.
5. Zed Attack Proxy (ZAP)
ZAP is a free, open-source tool for dynamic testing (DAST) of Web applications.
For this comparison, we tested ZAP for Windows using automatic and manual scans.
Who is it aimed at? Companies wishing to check the security of the web applications they currently operate.
Pros
- Ease of use: it’s very simple to install and launch automatic scans.
- Customisable reports.
- Heads Up Display (HUD) functionality, which lets you perform scans and view alerts while interacting with the site to be tested in the browser.
Cons
- High learning curve. Even if it’s quick to get to grips with, there are plenty of functions and configurations to choose from. It takes time to read the documentation and carry out tests to optimize its use.
- The application interface is not very user-friendly.
6. Wazuh
Wazuh is a SIEM and XDR platform. It’s open source and free, with a Cloud version available for a fee. For the purposes of this comparison, we installed the main components (Wazuh indexer, Wazuh server, Wazuh dashboard) on an Ubuntu 22.04.4 VM and a Wazuh agent on a Windows machine.
Who is it aimed at? Companies who want to start monitoring the security of their systems.
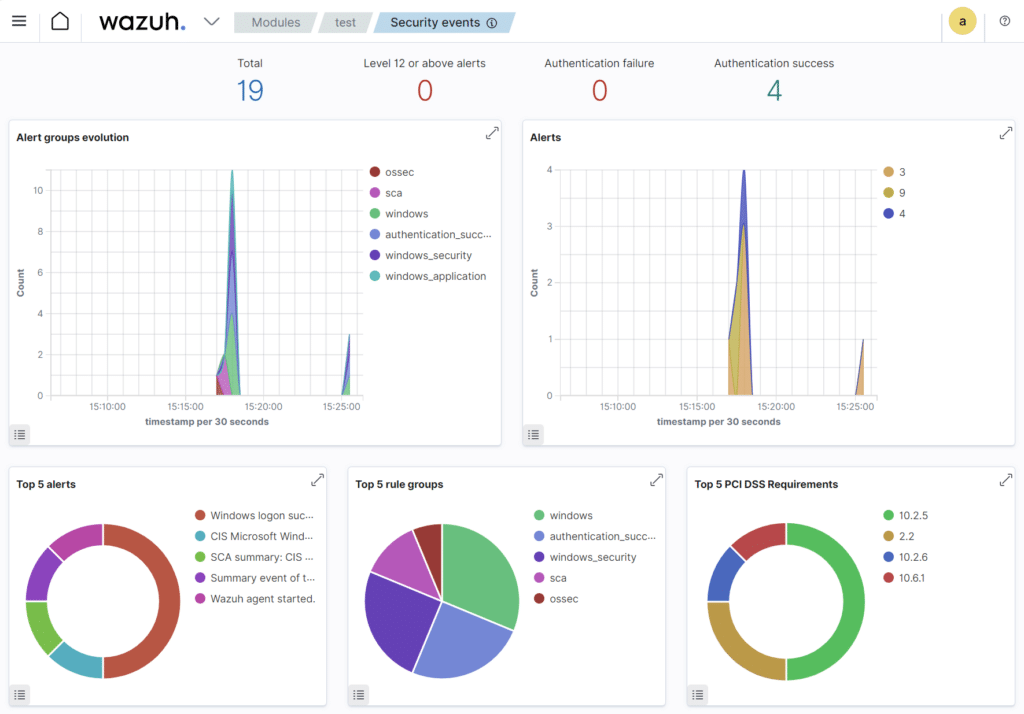
Pros
- The availability of agents for a wide range of systems (Linux, Windows MacOs, Solaris, AIX, HP-UX), allowing you to monitor a heterogeneous infrastructure.
- Easy to set up: both installation and operation are quick, requiring little effort.
Cons
- The Vulnerability Detector module is disabled by default.
- Some configurations cannot be carried out via the interface and require configuration files to be modified on the machine that is hosting the central components.
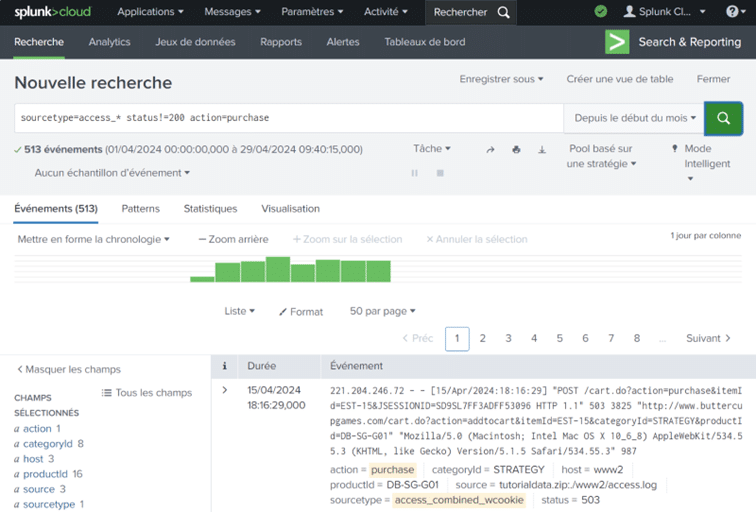
7. Splunk
Splunk is a SIEM and SOAR platform. As part of this comparison, we tested Splunk Cloud.
Who is it aimed at? Companies with specific needs who are ready to make an investment in their security provision.
Pros
- Numerous possibilities for integrating other tools with Splunk, for example to supply it with data.
- Data standardisation. Moving from a log line to a table of fields/values improves understanding and processing.
- Research and data processing. It’s possible to isolate several hundred log lines and easily obtain statistics about them.
Cons
- Handling. Splunk does provide tutorials, but it takes time to understand and test the many features.
- The price. There are 4 pricing options: workload, ingest, entity, activity-based. It’s therefore important to carefully assess what you actually need before selecting the right category of pricing.
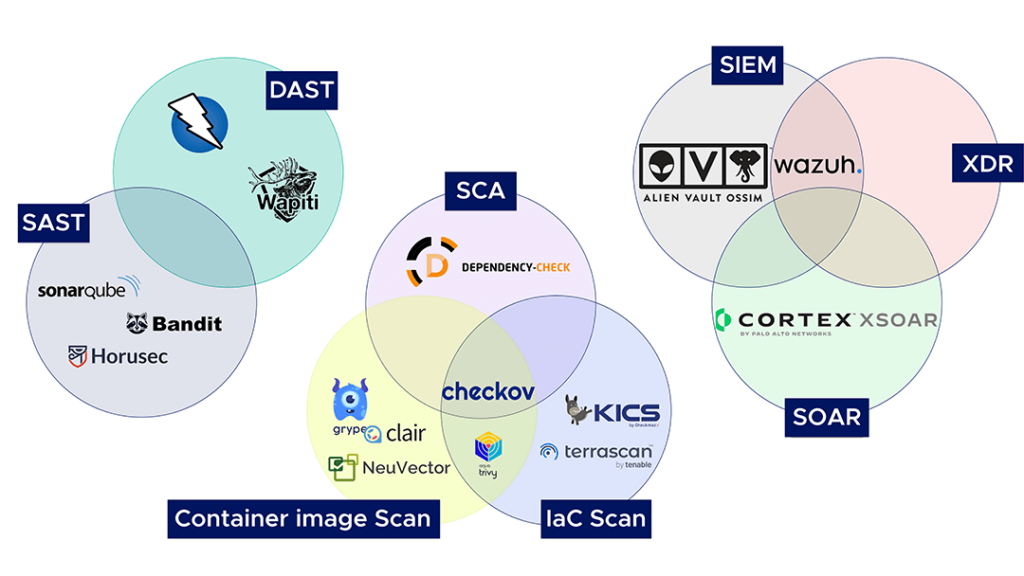
An overview of open-source DevSecOps tools
How can Qim info help you implement DevSecOps tools?
Thanks to its in-house experience, Qim info’s Cloud & DevOps Solutions department can help you choose and implement DevSecOps tools.
We can also provide consulting services if you’re new to DevSecOps or want to find out more about DevSecOps and its tools. Attending workshops can help you find the solution that is best suited to your needs. Depending on your activities, needs and constraints, Qim info can recommend tools to enhance the security of your projects.
In addition to this activity, Qim info can also help you implement and configure DevSecOps tools.
Conclusion
There are many different types of tools available to facilitate the implementation of the DevSecOps approach.
The important thing is to choose tools that meet your objectives and are adapted to suit your work processes. Make sure you give your teams the time and training they need to fully adopt these new tools.